Trojanized versions of the hugely popular FileZilla FTP client are being offered to unsuspecting users via hacked websites with fake content.
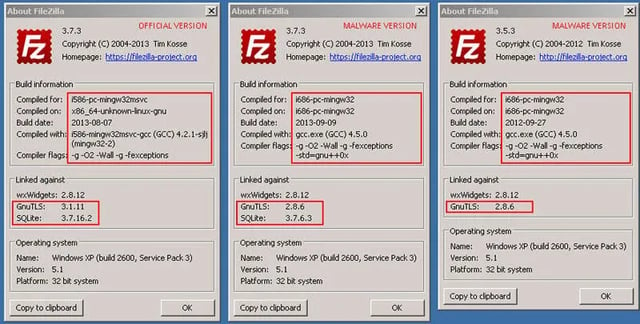
"Malware installer GUI is almost identical to the official version. The only slight difference is version of NullSoft installer where malware uses 2.46.3-Unicode and the official installer uses v2.45-Unicode. All other elements like texts, buttons, icons and images are the same," Avast researchers warn.
"The installed malware FTP client looks like the official version and it is fully functional! You can’t find any suspicious behavior, entries in the system registry, communication or changes in application GUI."
The malware records, encodes and sends FTP login credentials to the criminals' server hosted in Germany, the domains on which are registered with Naunet.ru, a Russian domain registrar known for malware and spam activity.
It's interesting to note that one of the malicious versions has been compiled way back in September 2012, and is still detected by just a couple of commercial AV solutions. Another one dates back to September 2013, and is also poorly detected.
"We assume that the stolen FTP accounts are further abused for upload and spread of malware. Attackers also can download whole webpage source code containing database log in, payment system, customer private information etc," the researchers pointed out. "Connection via infected FTP client to your home or corporate network is another level of this threat."
To avoid being saddled with a malicious FileZilla version, users are advised to download it only from the software's official website or from well-reputed download sites, and to avoid any unsolicited download offers.


